Security
Stay Ahead of Cyber Threats
Cyber security within the federal landscape is critical to protecting valuable data and organizational operations. The security realm is pervaded by a slew of dangerous threats, from brute force and social engineering to Distributed Denial of Service (DDoS) attacks, and without the right Cyber Security Solutions, environments are seriously fragile. A solid security posture is built by combining the right tools, techniques, and expertise to shore up areas of vulnerability, and both federal and enterprise organizations must give security adequate consideration to avoid irreparable damages.
Architecting the right solution to secure enterprise, cloud and big data environments is a lofty endeavor, but necessary to prevent breaches in a swiftly evolving compute landscape. In the event of a potential security threat, rapid response is imperative to minimizing damages. In terms of ongoing security practices, taking a proactive, rather than reactive approach, puts your organization in an improved position of defense, reducing the potential for breaches and related damages.
August Schell specializes in partnering with enterprises and government organizations to comprehensively assess organizational security posture and build cyber security solutions that fit unique needs.
OUR SECURITY SOLUTIONS
METHODOLOGY
The team at August Schell is comprised of security experts who have been working in the federal space since the company’s beginning. With extensive expertise in products and services across many security vendors, our goal is to select and engineer the ideal solution for addressing vulnerabilities and preventing breaches today and in the future.
- Identify areas of vulnerability
- Select the optimal tools for security needs
- Implement a comprehensive solution and enhance security posture
Micro-Segmentation
SECURE TRAFFIC WITHIN THE DATA CENTER
ZERO TRUST NETWORKS
Are you securing network traffic inside your network, inside the perimeter? Using micro-segmentation as a method of extending security within the data center, it is possible to safeguard traffic moving to and from each and every workload. Micro-segmentation enables a stateful firewall at every virtual network interface, enabling Zero Trust networking at scale.
MICRO-SEGMENTATION SOLUTIONS
Your data center has to be secured at the perimeter, now protect the inside of your network as well. Implementing micro-segmentation is a surefire way to enhance the security of your networks.
OBJECTIVES
- Zero Trust Networks
- Better visualization of network flows
- Enhance the overall security posture of your data center
- Prevent infiltration beyond the perimeter firewall
- Mitigate exfiltration attempts from within the data center
- Protect all virtual machine workloads through centralized firewall management
WHY AUGUST SCHELL?
- Ability to provide cleared resources
- Unparalleled technical expertise
- Rich history and proven track record
- Partnerships with top technology vendors
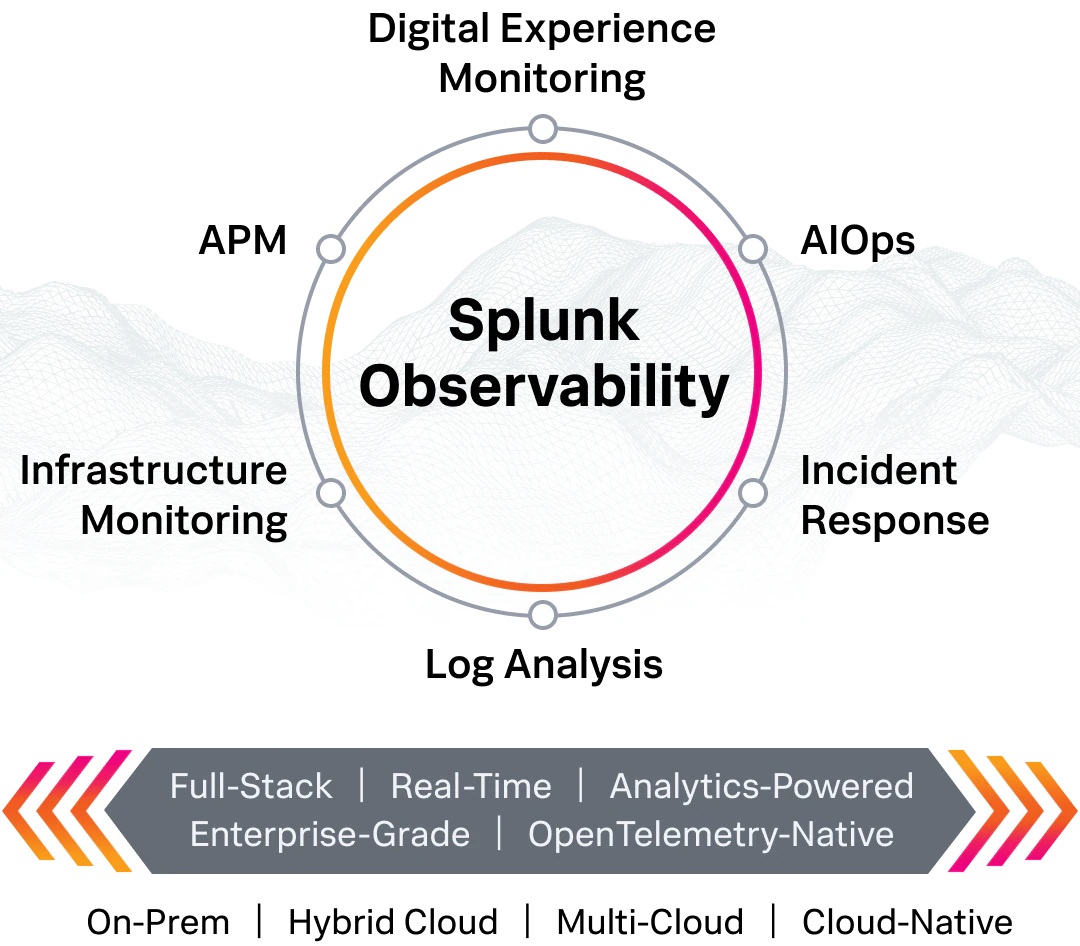
ENTERPRISE OBSERVABILITY POWERED BY SPLUNK
IMPROVE DIGITAL RESILIENCE BY LOWERING THE COST OF UNPLANNED DOWNTIME, IN ONE UNIFIED EXPERIENCE
FIX PROBLEMS FASTER
Guided root cause analysis, intelligent correlation and built-in incident response help teams spot and resolve issues 80-90% faster.
IMPROVE RELIABILITY
Predictive analytics and proactive business services monitoring helps teams reduce major IT incidents by over 50%.
BUILD EXCEPTIONAL END-USER EXPERIENCES
Gain a superhuman understanding of your apps, infrastructure and user’s experiences with open standards based, real-time monitoring, accelerating development by over 90%.
OBJECTIVES
- Enable smarter monitoring
- Enhance analytics capabilities
- Identify anomalies more quickly
- Optimize IT operations
WHY AUGUST SCHELL?
- Ability to provide cleared resources
- Unparalleled technical expertise
- Rich history and proven track record
- Partnerships with top technology vendors
IDENTITY ACCESS MANAGEMENT
MAINTAIN A RELIABLE PUBLIC KEY INFRASTRUCTURE, MANAGE DIGITAL IDENTITIES
PKI AND MOBILE DEVICE MANAGEMENT
Does your business manage digital identities through the whole of the organization? Are you maintaining a strong, properly designed PKI? Is your mobile ecosystem secure? With the takeover of mobility throughout business functions, it’s never been more imperative to utilize derived credentials through digital certificates for the identification, authentication, non-repudiation and authorization of users and endpoints—especially in the federal space. PKI and digital certificates offer a reliable solution for successfully managing digital identities and mobile devices while also providing the ability to protect the confidentiality and integrity of data.
IDENTITY MANAGEMENT SOLUTIONS
In order to keep your data center operating smoothly, it’s essential to integrate all operational data points to create a single view for making intelligent technology decisions.
OBJECTIVES
- Manage digital identities
- Manage and secure mobile devices by using derived credentials
- Enhance the overall security posture of your infrastructure
- Prevent breaches and outages
- Secure endpoints
WHY AUGUST SCHELL?
- Ability to provide cleared resources
- Unparalleled technical expertise
- Rich history and proven track record
- Partnerships with top technology vendors
Want to learn more about our Cybersecurity Solutions?
We can help you with your IT Challenges!