August Schell’s Security Validation
Featuring Mandiant
Security Validation is a continuous process
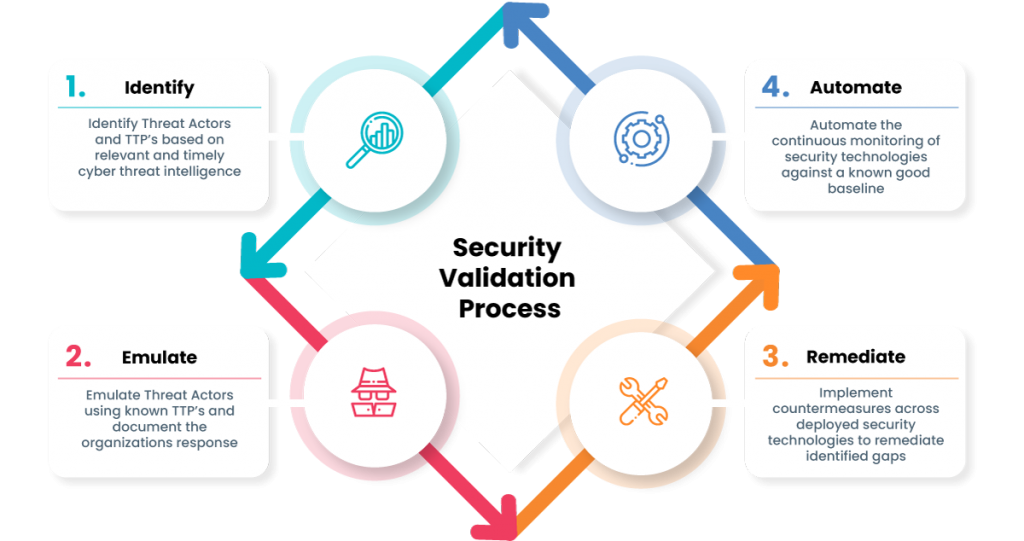
Answer the most difficult questions asked of a Cybersecurity organization with real-time quantifiable metrics.
“Are we protected against the latest cyber threats?”
- For years, Security Operations teams have implemented countermeasures to detect and prevent cyber threats. For many Security Operations teams, the countermeasure process stops after initial implementation without verifying they are functioning as expected.
- August Schell’s Security Validation Process gives operations teams the ability to validate the implementation of deployed security technologies and countermeasures using quantifiable metrics.
“Have operational changes impacted our security baseline?”
- Its no secret, Enterprise Information Technology Organizations are large and continually changing. Regular maintenance, troubleshooting, outage remediation, additional capacity, and new services are just a few activities that are occurring on a regular basis. Often, Security Operations teams are unaware of all operational changes occurring within the organization. This can lead Security Operations teams to believe security technologies are functioning correctly when they are not.
- August Schell’s Security Validation Process gives operations teams the ability to continually monitor the organizations security baseline and identify when operational changes have impacted the baseline.
“Do we have the right processes in place to respond to cyber threats?”
- Deploying security technologies and implementing countermeasures is only one part of cyber defense. Organizations need to ensure alerts are provided to the right analyst and incident response processes are followed.
- August Schell’s Security Validation Process allows cybersecurity organizations to run live exercises in their operational environment using relevant, intelligence driven, Tactics Techniques and Procedures. This provides operations teams with a repeatable, performance-based, process to verify the effectiveness of incident response procedures.
“How are our investments in security technologies performing?”
- Organizations make large investments into security technologies to mitigate threats and prevent cybersecurity incidents. As cyber threat actors Tactics Techniques and Procedures evolve, so do the defensive security technologies that are developed to protect organizations against them. This can lead to organizations investing in multiple security technologies that are performing the same function, outdated, or no longer functioning as intended.
- August Schell’s Security Validation Process provides decision makers with quantifiable metrics to accurately assess the performance of security technologies within their organization. This allows leadership to decide whether to continue with the current investments, remove an overlapping technology, or look at a new offering.
Service Offerings
Deployment and Sustainment
Looking to implement a Security Validation platform within your organization?
Let August Schell work with your organizations cybersecurity professionals to scope and deploy a Security Validation solution that is tailored to your organizations needs and requirements.
Already have a Security Validation platform deployed within your organization?
August Schell can assist your organization with technical improvements such as integrations with existing security technologies, expanding visibility across your infrastructure, and remediating failed components.
Process Integration and Improvement
Want to integrate Security Validation into your organization’s cybersecurity operations?
August Schell will work with your organization to integrate a Security Validation program into your daily operations that is tailored to your organization’s specific needs.
Looking to take your Security Validation team to the next level?
Have August Schell bring its real world Security Validation experience to your organization with a focus on improving your Security Validation process, techniques, and reporting.
Exercise Planning and Execution
Need to ensure your security operations processes and incident response procedures meet your organizational needs?
August Schell will plan and execute cyber evaluations based on the most current cyber threat intelligence and tailored to your organizational needs.
Want to ensure your organizations cybersecurity analyst continue to stay sharp and capable or responding the latest cyber threats?
Work with August Schell to develop and carry out cyber exercises that emulate the tactics, techniques, and procedures of advanced cyber threat actors.
